

|
Home
| Databases
| WorldLII
| Search
| Feedback
Australian Federal Police - Platypus Journal/Magazine |
Terror-vision
In an exercise in virtual-Darwinism, those who don't ‘switch on' in the new millennium might well find themselves on the endangered list.
By Leanne Lynch

Picture: NASA
The word ‘terrorism' immediately brings to mind images of exploding bombs and hostage situations in which one side tries to impose its will upon the other through what is effectively a game of chicken.
Traditionally seen as the province of those with a religious or nationalist axe to grind, terrorist incidents occurred in well-known hot spots and were aimed at soft but ideologically significant targets as a means of coercive diplomacy. Responsibility for incidents was quickly claimed - often by more than one group - in an effort to establish an identity and to foster sympathy for, or at least an awareness of, a supposed underdog's plight.
Moreover, terrorism was associated with discrete groups of homogeneous ethnicity that were usually centred on a charismatic leader. Like any hierarchical organisation, these groups had assets and possessions, rules and habits of association, and the identities of their leaders were often widely known - which allowed law enforcement and various security services to study, target and even infiltrate them.
But sometime between Victory at Entebbe and True Lies, perceptions of terrorism began to evolve, as those involved on the business side of things became less dependant on traditional hierarchies and more globally networked. Along the way, terrorists discovered that they could use technology to coordinate activities, raise funds, spread propaganda, contact like-minded individuals and groups and gather information on their enemies. The special effects got better, too, and the body count went up as perpetrators planned acts aimed at capturing the attention of a jaded public.
Counter-terrorism efforts now exist in a world where geographical and jurisdictional boundaries no longer impede the contagion of extremism limited only by money and imagination. The supporters of Osama bin Laden have access to almost unlimited funds and tacit support from several rogue States in what has become an ongoing war with the United States. Their methods thus far have been traditional, but have spread across the globe.
The members of the Aum Shinrikyo sect, while equally well-funded, hit ‘domestic' targets - although it should be remembered that their chemical weapons development took place in Australia and that they had more members in Russia than in Japan.
The nature of terrorism is evolving, but this is not to say that the older species will not coexist with the new. The matrix 'Four quadrants of terrorism', while not definitive, attempts to provide an identikit of the future faces of terrorism based on two axes: terrorist use of technology and violent intent.
Of the four quadrants, Armageddon and Revenge of the Nerds represent the rapidly evolving forms of terrorism, in which the use of technology shows innovation and is often at least one step ahead of the law. Actions taken that fit within these two quadrants will impact on a larger immediate volume of people than traditional terrorist events and may result in unforeseen collateral damage on an international scale.
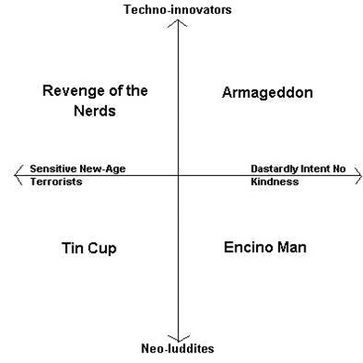
Four quadrants of terrorism
At the extreme points of the two quadrants - vis a vis technology - the former will most likely employ information technology as means to an end, whereas the latter will actually target information technology systems as the end itself. In practice, however, the divide may not be so stark.
The following scenario is drawn from a paper published under the auspices of the US Institute for National Strategic Studies:1
By accessing the CNN weather forecast, an extreme Serbian paramilitary group times an attack on an airfield for a night of intense storms in the Brcko area, and then, using hacking tools, intrudes on the frequencies of the approach and tower radios. In the storm, flying with navigation lights off due to reported ground fire, a full C-130 troop transport is cleared to land by the approach intrusion. Another C-130, laden with fuel and also with its lights off, is cleared for take-off on the active runway by the tower intrusion. The two planes crash and all aboard are killed. Immediately afterwards, the hackers issue an e-communique via an anonymous web service account in Finland which is sent to every major print and electronic news organisation in the industrialised world as well as to an extensive private email list.
Twenty-four hours later, the group's web page has received more than one million hits. Twenty-four hours after that, the systems of those who had accessed the page began to crash, irretrievably deleting files, as a result of an embedded Trojan horse.
Armageddon-style terrorism will be recognisable by a global network that enables events to be directed with relative anonymity. It will be international in nature, utilise a structure of independent cells and ‘cut-outs' (amateur patsies), and tend to be religion or ideology based - although nihilistic objectives can not be ruled out. Its goal will be terrorism as a form of war or the creation of a ‘brave new world' from the ashes of what it seeks to destroy. Rather than intermittent attacks in retaliation for perceived injustices, the war paradigm of Armageddon will mean an almost unceasing threat for the duration of the conflict.
The occupants of quadrant Armageddon will not feel a need to explain their actions by claiming responsibility - believing actions speak louder than words. At its most extreme level - known as ‘superterrorism'2 - violence will be planned on a large scale and collateral damage of innocent bystanders and the infrastructure of society will be welcomed as a bonus. Nuclear, biological or chemical warfare tactics are most likely to be utilised within this quadrant.
A scenario contained in an edition of the Jerusalem Report3 shows how easy, and devastating, such attacks might be.
"After arriving on a plane from New Delhi, a man in a business suit drops a bag containing an old deodorant dispenser into a trash can at Ben-Gurion International Airport's arrivals hall. An hour later, the timed release of wisps of VX gas, which causes death almost instantly on contact with the skin, kills hundreds of people, among them the first wave of security and emergency personnel."
Armageddonists will be well versed in the use of technology and will utilise it to its maximum potential for both operational and administrative purposes. They will use satellite phones and sophisticated encryption devices on their lap top computers. They will raise funds for their activities globally via the Internet and launder them in offshore tax havens. They will be pro-active in gathering intelligence and will employ many of the same methods used by law enforcement and the security services, or pioneer more advanced ones. They will purchase protected technology and substances from rogue States when they can, develop their own when they cannot, and sponsor the education of promising proteges to the schools of Western countries in order to stay on top of advancing methodologies.
Wannabe Armageddonists: The white supremacist and millenarian American Covenant, the Sword and the Arm of the Lord, whose chemical-weapons stockpile was seized by the FBI in 1985 as they prepared to hasten the coming of the Messiah by poisoning the water supplies of several US cities.
Nerd-style terrorism is a mutation of the passive resistance methods of the sensitive sixties. Like the Armageddonists, Nerds are internationally networked but in their early evolvement were ideologically founded rather than religiously motivated - although this is not necessarily a static situation. Again, action based on nihilistic motives - destruction for destruction's sake - will become increasingly common within this quadrant. On the whole, however, Nerds will tend to seek symbolic, disruptive action on a large scale rather than violence against individual persons.
Their networks will be looser and tend to comprise information-sharing like-minded individuals. Their weapons will be computer viruses, worms, logic bombs and bots, and their targets will be the information and control systems of adversaries perceived as being ideologically flawed. This may include banking systems and money markets, air traffic control or city traffic flow mechanisms, the corporate networks of large companies or government departments, or the power and water networks of large metropolitan areas in digital attacks that are notoriously difficult to source.
Nerds may also seek to access and disseminate sensitive information as a mischief - and in some cases will be used for this purpose by less technically-minded but more sinister habitues of other quadrants. Take the case of an 18-year-old California cracker, who calls himself Chameleon, suspected by the FBI of selling US military secrets to a member of the Pakistani terrorist group Harkat-Ul-Ansar.
"I went to my post-office box one morning, and there was US$1000 with a number to call in Boston," said Chameleon.4 Khalid Ibrahim was allegedly seeking maps of US government computer networks that Chameleon had obtained on his travels through the Net. Chameleon cashed the cheque but did not hand over the information. He was not charged and, in a classic case of a chameleon changing colour, has since put down his hacking tools to become a security consultant.
Cyber terrorism is one of the two top post-Cold War problems the world faces, according to Raisuke Miyawaki, senior adviser to Japan's Committee on Critical Infrastructure and chairman of a think-tank that advises Japan's largest companies on organised crime and terrorism. In June 1999, he predicted that "it is only a matter of time" before all nations experience the first cyber attack on a worldwide scale.5 As it is, the US Defence Department alone is said to get 60 to 80 hacker attacks a day.6
In what has been labelled by some as a ‘Pentagon ghost story', the National Security Agency launched Operation Eligible Receiver in 1997.
Using software obtained from Internet hacker sites, NSA agents gained access to computer systems controlling the US electricity power grid, the 911 emergency telephone system, and US Pacific Command in Hawaii, giving them the potential to shut down city power systems or even disrupt troop movements. In particular, they showed that large-scale blackouts could be caused by targeting computerised sensing and control devices - devices that are also used as common substitutes for human monitors in operating electrical, oil, gas, transportation and water treatment systems.7
In practical terms, imagine Queensland's blackouts, Sydney's water crisis and Victoria's gas disaster happening simultaneously along with a complete shutdown of rail and traffic control systems.
A simple example of the power of cyber attacks occurred in 1997, when a flood of email originating in Australia and Estonia - and routed through the White House computer system - virtually shut down Langley air base's email for hours. At the same time, someone in England routing messages through Latvia, Colombia and Chile and commercial Internet service providers gained access to computers at Rome Laboratory, Griffis air base, and launched attacks against a wide array of defence and government computer systems.8
In Japan, groups have attacked the computerised control systems for computer trains, paralysing major cities for hours, while in Mexico, Sri Lanka and Indonesia, government networks were crashed during recent elections.
A particularly virulent weapon of the Nerd is the mere threat of action. The more dependent a society (or a particular element of a society) is on technology the greater the leverage of the information terrorist.
Even more than the cell structure and heightened security methods of the Armageddonists, the modus operandi peculiar to this quadrant means that its occupants can confidently hope to maintain complete anonymity as they wreak havoc. They can work from home, never meeting each other in real life. More importantly, they can launch an attack from a completely different country, leaving no physical evidence and not having the discomfort of seeing the effects of their work up close.
Proponents of Nerd-style terrorism will often have an intellectual superiority complex and, while not prone to claiming responsibility publicly, may be unable to resist bragging in their own alternative forums.
Prototype Nerds include: David L. Smith, 30, of Aberdeen, NJ, who was arrested and charged with originating the email virus known as Melissa; and Ehud Tenebaum, the suspected mastermind behind what the US Government described as "the most organised and systematic [cyber] attack the Pentagon has seen to date."9
The occupants of quadrants Encino Man and Tin Cup are buffeted by the winds of technological change rather than soaring upon them to greater heights of endeavour, and will tend to operate more in the domestic arena than on the global stage.
But while the occupants of quadrant Tin Cup represent the typical champions of obscure local causes and lack any real capability or stomach for the wet work of their more fanatical cousins, the occupants of Encino Man represent terrorism in its tried and true form and remain a real threat.
Terrorist acts perpetrated within this quadrant may well be violent, but will be organised domestically on a relatively contained scale, aimed at self-explanatory targets and often claimed publicly. For Australia, this is not to say that the issues at hand will necessarily be ‘domestic' in the true sense of the word. Our society is multicultural, and historically most of the terrorist incidents that have occurred here have been influenced by events overseas.
Lack of technical evolvement does not mean that Encino Men despise the new technologies. A recent report by the US Anti-Defamation League found that hate groups are stepping up their use of the Internet to seek new recruits, and are becoming ever more sophisticated at targeting children.10 Another report by the US Department of Justice found pointers to 110 bomb making texts via just a single website.11 The DoJ report also revealed the frequent use of ‘Usenet' newsgroups to facilitate the exchange of information concerning the fabrication and use of explosives and other dangerous weapons.
Since the 1995 bombing of the Alfred P. Murrah building in Oklahoma, there has been a disturbing increase in the incidence of politically motivated crimes in the US. Before Oklahoma City, the FBI had only 100 open domestic terrorism cases; today it has over 1,000. According to experts this is almost certainly a product of the move from traditional hierarchies to a system of organisation known as ‘leaderless resistance', recognisable by its cell-like, networked structure.12
Even more disturbing is the hypothesis that as groups learn to use IT for decision making and other organisational purposes, they will be likely to use the same technology as an offensive weapon to destroy or disrupt13 - suggesting a kind of "bracket creep" up the y axis of the matrix. Another factor that will contribute to bracket creep is that younger recruits will tend to be increasingly well versed in the use of technology.
That the nature of domestic conflict is changing has been recognised, in the US at least, where strategists envision a future battlefield defined by stateless war in an urban terrain, against threats including "criminals with computers" and "terrorists searching for weapons of mass destruction".14 To prepare for such a future, the US Marine Corps Warfighting Laboratory created the Urban Warrior exercises - a series of limited objective experiments examining new urban tactics and experimental technologies.
Of course, such battlefields have already become reality in some countries, with the rise of narco-terrorism and transnational crime blurring the lines between national security and law enforcement.

A US Marine rushes to his objective during Urban Warrior 1998. Picture: Department of Defence.
No less dangerous than their upper quadrant colleagues, Encino Men at least represent a comfort zone for law enforcement and security agencies. Their methods are familiar and they have usually not outstripped their opposite numbers in the use and understanding of technology - yet.
Other Neanderthals have been found at: Ruby Ridge, just about anywhere in the US State of Montana, and in the offices of Lock, Stock and Barrel magazine.
Quadrant Tin Cup in this paper is populated by individuals and groups that attempt to change situations and events they see as untenable via usually non-violent means. On the whole, those in the Tin Cup are usually people who concern themselves with emotive local issues and whose main exercise comes from jumping on bandwagons. They will be vocal placard bearers and regular contributors to editorial columns and talkback radio.
While of less interest to environmental scanners and forward planners than the other three quadrants, the Tin Cup is sometimes the kindergarten of future serious players, who steadily work their way up the extremist scale from one group to the next. In addition, it is not unheard of for random individual acts of terrorism to originate from over-zealous occupants of the Tin Cup, something particularly difficult to predict or guard against.
And the Tin Cup is awarded to: the man who made a death threat via the Internet using his ISP email - not realising it listed his real name as well as his chosen pseudonym.
Cyber-terrorism is a result of the Internet, not just computer technology. Ed Roche of the Concours Group, an international firm that studies Internet security issues, says "Terrorism certainly existed before the Internet, but in order to do it, you had to be there. With the Internet, a group in, say, Madras, India, can bring down Con-Ed."15
That conventional terrorism owes its evolution to technology is indisputable, with advances in weapons technology and availability meaning that death on a grand scale has become more a question of engineering or biochemical knowledge than of passion. The Internet, too, is providing that little knowledge which can so often be a dangerous thing. Several Internet sites provide data on Semtex - less than 300 grams of which was enough to destroy Pan Am Flight 103 over Lockerbie, Scotland - while about 400 sites discuss sarin, a Nazi nerve gas so lethal that a single milligram quickly kills.
There is a saying that "terrorists want a lot of people watching, not a lot of people dead".16 And if this is so, it is communications technology that has been the main driver of the trend towards what has been called ‘terrorism spectaculars',17 for without an audience terrorism loses much of its efficacy. Indeed, the public expects to be able to follow an incident almost as if they were participants rather than onlookers.
On December 17, 1997, for example, 14 members of the Tupac Amaru Revolutionary Movement (MRTA) took hundreds of high-level diplomats, government and military officials and business executives hostage during a party at the Japanese ambassador's residence in Lima, Peru.
The world received live television coverage of the siege, which lasted for four months, including its dramatic ending when all 14 terrorists were killed during the commando raid that freed the remaining hostages.

The Peru hostage crisis in 1997 brought terrorism into the loungeroom during the four month seige.
And yet not all observers were particularly impressed by the technology that allowed CBS television to cover the event from takeover to rescue. "Though dramatic, such immediate on-the-scene coverage is no longer surprising. In fact it is expected, and any ‘technical difficulties' are greeted with disdain…" said John Haystead of Wireless Integration magazine.18
The MRTA were also revealed to be quite knowledgeable about the power of the media. A Peruvian television station broadcast videotape that showed MRTA members - dressed in military style clothing and with their faces covered by scarves - preparing for the assault by studying a mock-up and photos of the Japanese ambassador's compound.
Then, during the hostage stand off, the MRTA sent emails to the press saying they were social fighters, not terrorists, and that they respected international human rights conventions. After the siege, three men broke into a cable television station in Colombia and forced the crew to assist them to broadcast a message of retaliation.
Despite predictions and scenarios, the odds of a major biological, chemical or cyber terrorist attack are nowhere near as large as that of a conventional terrorist incident involving car bombs or hostage taking. However, when making risk assessments, it is necessary to consider the potential impact should such an incident occur. In any of these cases the results are so unthinkable as to demand that contingencies be in place.
The rapid advancement of technology and its potential to impact upon the work of government agencies has been noted and acted upon in some spheres already. In Australia, one of the goals of the AFP's reprofiling program has been to position the agency to fight crime in an increasingly technological environment, while proposed changes to the ASIO Act will reflect the new challenges and opportunities presented to that agency by new technologies.
In the US, the recent creation of the National Infrastructure Protection Center and the Joint Task Force on Computer Network Defense reflects the Pentagon's increasing emphasis on cyber defence and its recognition of the likelihood of computer attacks by nations, hackers and terrorists.
Conventional counter-terrorism efforts have also recognised the importance of technology and the benefits of networks comprising members of law enforcement, military and intelligence agencies, as well as representatives of emergency services and state and local government. In other words, fighting fire with fire.
All too often, though, the devil is in the less-sexy detail. The ‘smaller' issues that planners must address - if they hope to meet the challenges of the new millennium, that is - include:
• The need to keep up with technological advancements without becoming so reliant on technology that all response capability grinds to a halt should a ‘melt-down' occur.
• Jurisdictional and cross-departmental confusions that may arise when incidents do not fit into the pigeon holes of existing planning models.
• The State-less nature of the Internet and the implications of foreign providers of email, web sites and offshore banking services.
• The impact of global mobile phones and trend towards cross-pollination of communications technology.
• The increasing legitimacy and accessibility of Internet news groups and chat lines as a valid form of media that must be serviced.
• The potential of the Internet as both a source of intelligence and of information overload.
Predicting trends in terrorism is a tricky business, and I have neither a crystal ball nor the last name of Nostradamus. However, then-CIA Director John Deutch told a senate subcommittee in 1995 that his agency had evidence that "a number of countries around the world are developing the doctrine, strategies, and tools to conduct information attacks".19
In fact, in December 1998 the Centre for Strategic and International Studies, a Washington think-tank, warned that US law enforcement agencies were five to 10 years behind the transnational crime curve. In particular, its members were of the opinion that, if properly prepared and coordinated, and with a budget of less than US$10 million, 30 computer experts strategically placed around the world could bring America to its knees.20
In 1998, the Washington Times revealed that the Pentagon had quietly buried one of the most comprehensive reports ever commissioned on the changing patterns of global terrorism,21 a document titled Terror 2000.
The Terror 2000 findings, compiled by 41 experts including former ranking CIA, FBI, State Department and RAND Corp officials, as well as an ex-KGB general and Israeli intelligence agent, were deemed too alarmist and far-fetched. Even a sanitised version designed to promote public preparedness was axed.
The only catch is that many of its predictions have since come true.
One of the report's fundamental conclusions, endorsed by a host of independent experts, is that trends in terrorism will continue to mutate in the post-Cold War world. In particular, Terror 2000 envisioned a volatile period distinguished by global superterrorism, involving sporadic but sensational attacks, often featuring advanced weaponry.
In one uncannily accurate prediction, the report warned that extremists may try to maximise their impact by moving beyond one-at-a-time attacks to multiple, simultaneous targeting, thus demonstrating their reach and taxing the ability of governments to respond. And this is exactly what happened in Africa, when the two car bombs exploded within minutes of each other outside the US embassies in Nairobi and Dar es-Salaam.
The report also outlined fictitious plot lines for simulations played out like war games between US counter-terrorism teams, including the release of a chemical nerve gas in the New York subway system - a scenario similar to that of the Aum Shinrikyo sarin attack in the Tokyo subway in 1995.
According to Dr Donald Henderson, the director of the Centre for Civilian Bio-defence Studies at John Hopkins University in Baltimore, US experts expect a bio-terrorist attack to occur within the next decade.22 And no country, including Australia, has taken adequate precautions, Dr Henderson said, speaking at an international microbiology conference in Sydney in early August.
In real terms, what might this mean? Well, Peter Probst, an analyst at the Pentagon who composed an anthrax scenario for Terror 2000 has noted, "The death toll [of a bio-terrorist attack] would be horrific. And you can't bury the victims. You have to burn them. There would be funeral pyres throughout the city."
Also of concern to planners is the strain that would be put on the public health system by the ‘worried well', people who wrongly believed they were infected.23
It is little wonder then that the Australian federal government is spending $23 million on equipment to protect the defence forces against germ warfare, chemicals and radiation, in an acquisition program called Project Bloodhound.24
Overall, Terror 2000 predicts eight to 10 years of "tumult and transition" terrorism, and other forms of low-intensity conflict, until the rules of the post-Cold War world are better established. In the end, it suggests terrorism will level off and perhaps even decline. "In the future, we expect peace settlements in many areas where violence has originated - in the Middle East, Northern Ireland, Yugoslavia, Russia and its neighbors," project director Creton predicted. "But it will take time. And during that time terrorism is going to get worse before it gets better."
Indeed, the authors of the RAND report and those of the US State Department's Patterns of Global Terrorism believe that the lethality of terrorism is increasing, despite the decline in the total volume of incidents. And one of the reasons for this, the RAND authors postulate, is that at least some terrorists have come to believe that attention is no longer as readily obtained as it once was.
Old-fashioned terrorism, new-age cyber-terrorism, conflict, genocide and war - even criminal threats, intimidation and acts of violence - all contribute to that which is called terrorism. How nation-states acknowledge, prepare for and deal with the spreading tide will mark the future boundaries of terrorism for their citizens.
There are those who, as always, question how far a government can go to protect itself and society before infringing on personal liberties. A member of a Boston-based network security group called L0pht believes that there are two buzzwords in government right now: paedophile and terrorist. "And any law or any measure taken against these two groups seems to be condoned by the public," he said. "It's the 90s equivalent of McCarthy's stand against communism."25
But there is a big difference between crying ‘reds under beds' and lapsing into a Pollyanna-like state sure that everything will work out fine in the end.
Unfortunately, it sometimes takes a hard lesson to overcome human kind's Pollyanna gene.
In the US, for instance, despite soothing words and hysterical references to the Constitution and Bill of Rights, the powerful gun lobby has taken heavy body blows in recent months. Highly publicised school yard massacres are finally forcing a reluctant public to admit that perhaps interpreting the Bill of Rights as the right of a 13-year-old to a military style assault weapon is stretching the point.
In the former Soviet Republic, old-fashioned bombings are enjoying a Renaissance as the disenfranchised, disenchanted or simply discombobulated express themselves outside the socially acceptable framework of legal protest. In Mexico, kidnappings and murder have become big-big business. In Africa, Asia and the Sub-Continent, genocide is, one might say, alive and well.
In Australia, the East Timor crisis has focused public attention on our defence capability - a capability that has been described by some as lacking real teeth. And yet, in the past, so-called bloated defence budgets were seen as a ‘soft target' - as were the resources and powers of law enforcement - by the same groups that screamed loud and long for Australia to send in the peace keepers and be quick about it.
Perhaps the biggest challenge to be faced, vis a vis terrorism in the new millennium, will be facing up to the fact that the world is shrinking and along with it Australia's famed protective shell - the tyranny of distance.
In 1859, Charles Darwin wrote a book called The Origins of Man, in which he stated:
Can we doubt that individuals having any advantage, however slight, over others, would have the best chance of surviving and of procreating their kind? It may metaphorically be said that natural selection is daily and hourly scrutinising, throughout the world, the slightest variations; rejecting those that are bad, preserving and adding up all that are good; silently and insensibly working, whenever and wherever opportunity offers.
The more things change . . .

Picture: NASA
1. M. Devost et. al., "Information Terrorism: Can You Trust Your Toaster?", Sun Tzu Art of War in Information Warfare, Institute for National Strategic Studies, 1998.
2. E. Sprinzak, "The Great Superterrorism Scare", Foreign Policy, Fall, 1998.
3. L. Susser and Y. Haran, "A Silent Terror", Jerusalem Report, 29/3/99.
4. N. McKay "Cyber Terror Arsenal Grows", Wired News, 19/10/98.
5. B. Woods, "Worldwide Cyberterror Attack Now A Question Of When, Not If", Newsbytes News Network, 29/6/99.
6. G. Barker, "Australia: Internet terrorism escalates the new infowar", The Age, 13/7/99
7. P. Cole-Adams, "Warning over cyber attacks", Sydney Morning Herald, 25/3/99; The Crypt Newsletter (e-zine).
8. Montreal Gazette, The Associated Press, 8/10/97.
9. "Hackers hit US defense system", Reuters, special to CNET NEWS.com.
10. Poisoning the Web: hatred online, Anti-Defamation League, June 1999.
11. US Department of Justice, "Report on the availability of bombmaking information, the extent to which its dissemination is controlled by federal law, and the extent to which such dissemination may be subject to regulation consistent with the first amendment to the United States Constitution", submitted to the US House of Representatives, April 1997.
12. D. Neiwert, "The threat from within", MSNBC.com.
13. Countering the new terrorism, RAND, 1999.
14. G. Smith, "One Nation Under Guard", Refuse and Resist e-zine, 20/3/99; N. Steinberg, "Marines land here to study for urban battles of future", Chicago Sun-Times, 5/5/98.
15. T. Regan, "When Terrorists turn to the Internet", The Christian Science Monitor, 1/7/99.
16. B. Jenkins, "Will Terrorists Go Nuclear?" Orbis, Autumn 1985.
17. Countering the new terrorism, RAND, 1999.
18. Wireless Integration, July/August 1977.
19. J. Elliston, "The CIA and Cyberwar: an electronic Pearl Harbor?", America On Line.
20. "America vulnerable to just 30 experts", The Canberra Times, 21/12/98.
21. R. Wright, "Prophetic ‘Terror 2000' Mapped Evolving Threat", Sunday Times, 9/8/98.
22. D. Smith, "Games ‘germ attack' fear", Sydney Morning Herald, 9/8/99.
23. S. Brook, "Games terror bugs under microscope", The Australian, 16/8/99
24. Ibid.
25. N. McKay "Cyber Terror Arsenal Grows", Wired News, 19/10/98.
AustLII:
Copyright Policy
|
Disclaimers
|
Privacy Policy
|
Feedback
URL: http://www.austlii.edu.au/au/journals/AUFPPlatypus/1999/32.html