
Journal of Law, Information and Science


|
Home
| Databases
| WorldLII
| Search
| Feedback
Journal of Law, Information and Science |

|
Online Privacy in Thailand: Public and Strategic Awareness
PIRONGRONG RAMASOOTA[*] AND SOPARK PANICHPAPIBOON[**]
This study examines the current state of awareness of privacy in Thailand, with two important foci — general online users, and leading members of civil society related to the area of privacy advocacy. In the absence of a data protection law and amidst long information surveillance practices administered mainly through the security state, Thailand posits a unique setting for a research inquiry into privacy awareness and future advocacy in the area. The study is carried out using two methodologies — a questionnaire-based survey with online users throughout the country, and in-depth interviews with selected members of social activist groups. Survey results show that patterns of privacy perception, levels of awareness, and reaction to privacy threats are variably influenced by factors such as socio-demographics, cultural attitudes, and online use characteristics. Meanwhile, public education is found to be the preferred option for promoting greater social awareness. Civic leaders feel that the main threats to privacy and hindrance against social awareness on the issue lie in the following: lack of fair information practice principles, prevailing discourse of national security, unaccountable use of cybercrime law to probe into people’s private data, and cyber lynching and witch-hunts of political dissidents. They also feel that public education focusing on the affected case along with the use of human rights discourse within an international legal framework are preferred courses of actions towards the mobilisation of privacy awareness in Thailand.
While globalisation has entailed a series of policy convergence across the globe, one area that has not been smoothly integrating is that of privacy. The concept of privacy signifies individualism, liberalism, public-private divide, and the rule of law, all of which underpin liberal democracy widely espoused in the West, but not so in other regions of the world including Asia.[1]
Such notions are simply not present in the context of Thailand, a Southeast Asian nation with an extensive history of state surveillance. From the ancient to the modern period, extensive collection of people’s personal information has been a long-standing practice. Ancient Siamese states[2] collected personal information of their commoners’ population through registration rolls and a coded wrist-tattooing system. In the modern era, the state keeps its population under bureaucratic surveillance through citizen ID cards, household registration passbooks, social welfare cards, and so forth.
This surveillance trend is also reflected in an important law — the 1991 Civil Registration Act — which was enacted in response to the introduction of computerised record-keeping and data-processing. While regulating the collection and use of personal information by the department of local administration which houses the civil registration bureau, the law notably allows other government departments to share in the use of civil registration information through requests for copies of information as well as through computer linkage.
Although there are a number of articles in different legislation and the constitution that address matters related to privacy in its multifarious dimensions, these provisions mainly deal with privacy in conjunction with other rights and legal protections. There are no direct stipulations about violations of privacy per se, since abuses typically have been framed in terms of trespass, defamation, or breach of trust or confidence instead.
Like most statutes on rights and freedoms in Thailand, privacy-related laws have historically been subject to limitations on the basis of collective public interests such as national security, public safety, and preservation of good morals. Such exceptions have tended to gravitate toward a norm in Thailand, given the country’s extensive history of dictatorial rule, its unique security situation as a buffer state during the Cold War, and the constant threat of a coup d’ état.[3]
However, after the country had shifted towards industrialisation in 1990s, efforts have been underway in the past decade and a half to draft and pass a data protection law, along with five other information and communication technology (ICT)-related laws. However, of these, only two laws have been passed — the Electronic Transactions Act 2001, which also endorses digital signature, and the Computer Crime Act 2007. Like in many countries around the world, the drafting of the data protection law was influenced by two landmark documents; the 1980 Organization for Economic Co-operation and Development’s (OECD) Guidelines on Protection of Privacy and Transborder Flows of Personal Data and the 1995 European Union Directive on Protection of Personal Data and Transborder Flow of Such Data.[4] Since the draft law is still in the legal pipeline, Thailand has referred to other provisions in related laws to address issues related to personal data, eg the Civil Registration Act 1991, the Official Information Act 1997, and the Computer Crime Act 2007. But these laws provide no equivalent alternative to a strong and enforceable data protection law as envisioned in the EU Directive. Without an explicit data protection law in place, several data surveillance schemes have been administered in Thailand at least since 1981 without adequate legal safeguards. For instance, the computerised and online civil registration system, the microchip national ID card system, the computerised criminal records database system and surveillance cameras in public areas.[5]
With regard to public perception of information privacy, it is academically safe to say those at the upper socio-economic strata are more apprehensive about privacy rights and threats from personal data collection and use. This is supported by findings derived from a series of focus groups on surveillance and privacy conducted in Bangkok in 1996.[6] Focus group participants from lower socio-economic groups were found to be ignorant about surveillance practices and oblivious to the privacy ramifications of such practices. Similarly, a 2001 survey on 1 200 Internet users showed that education and income are positively correlated with privacy awareness. The same research also found that 70 per cent of Internet users recognised their privacy rights online but only 50 per cent knew what action to take when faced with data abuses.[7]
In continental Europe, awareness of data protection and privacy issues driven by new technological challenges is also on the rise. Thus, a group of researchers conducted a meta-analysis of public opinion surveys on public understanding of data protection and privacy in Europe and found that the European public gave significant importance to data protection and privacy.[8] The privacy of personal information was ranked 3rd in order of importance, of these, 84 per cent regarding it as ‘very important’.[9] However, the public’s understanding was superficial on some more subtle aspects of privacy and limited to the letter of protection.[10]
In recent years, new Internet applications like social networking services (SNS), (particularly Facebook)[11] have emerged as popular communication tools among young people in Thailand and with them dawn new privacy challenges; for instance, the unintended consequences of posting sensitive personal information — text as well as photos, and confusion over privacy settings. While Thailand’s capital — Bangkok — has the highest number of Facebook users in the world at 8.682 million and Facebook penetration in Thailand is 22.01 per cent compared to the country’s population and percentage of overall Internet users at 83.60 per cent,[12] little awareness has been raised about the privacy implications of these popular applications. In considering socio-demographic and Internet use variables, previous research indicated that gender, Internet usage frequencies and Internet experience had no statistical significance to privacy behaviours. However, users with higher Internet usage skills applied higher advance technical protection.[13] A study by Paine et al, also found that the age of users and online privacy awareness are statistically significant, while number of hours spent using the Internet per week and years spent using the Internet had no relation with online privacy awareness.[14] In the context of Facebook, gender plays a crucial role on determining disclosure of information. Females seem to disclose less sensitive information than males.[15] Females, in Hoy and Milne’s study, were also found to engage in privacy protection behaviours more than males.[16]
On a more serious note (and in the recent context of cybercrime law enforcement), local Internet advocates and media have posited privacy rights as being undermined by law enforcers’ zeal to track and crack down on sources of rumours surrounding the Thai king’s ailing condition.[17] This incident has been reported on the CNN website under the headline ‘Police arrest two suspects in stock rumour case’.[18] After the arrest of the two suspects, who had posted the ‘problematic information’ in two popular online forums, the technology crime suppression unit of the Thai police reportedly sought court orders to look into email communication of all the people who have posted, on related topics, in the two forums.
Based on the widespread popularity of SNS in Thailand and the arrest case noted above, it could be argued that not only are newer applications like SNS prone to privacy violations, but classic applications like email have been no exception. Likewise, both information and communication dimensions of privacy are viably under threat in the current Thai context.[19]
Meanwhile, there is a dearth of direct advocacy in Thai civil society when it comes to privacy. Local NGOs working in the areas of information and communication are mainly focused on freedom of expression, freedom of information, consumer protection, intellectual property, and access rights. Interestingly, there is no identifiable civic entity whose main flagship is privacy. The last time a privacy issue emerged at a public level, it was advocated by a consumer protection NGO who viewed the mass texting of greeting message from then incoming Prime Minister Abhisit Vejjajiva to all mobile phone users as a violation of privacy.[20]
Since 2006, there have been three occasions in which a data protection draft law almost made it on to the legislative agenda in Thailand. On each of these occasions — August 2006, October 2009, and August 2012, three different Cabinets from three different administrations agreed in principle to enact the data protection law and forwarded the law to the House of MPs for a reading. The first process was abruptly halted after the 19 September 2006 coup when the military junta dissolved parliament and appointed an interim government and interim legislature. The second one was kept in the waiting list and never made it to the House Commission’s reading phase. The third one, after the ruling Phuea Thai Party-led Cabinet’s approval, was also forwarded for the House reading, however, shortly after a selected pool of commissioners were appointed to table the draft bill, the process was cut short by the sudden dissolution of the House by embattled Prime Minister Yingluck Shinawatra, under severe pressure by the anti-government movement called the People’s Democratic Reform Committee (PDRC).[21]
Based on an analysis of the latest draft law, if passed, it would establish a Committee on Data Protection to regulate policies, standards, and guidelines regarding the protection of personal data. The Committee would further establish a Personal Data Inspection Board, which would specifically be responsible for examining and considering personal data disputes.
The draft act would apply only to individuals and the private sector. It would not have authority over government agencies, which are subject to the Official Information Act, entities using and/or disclosing personal data for the purposes of mass communications or for literary purposes, or any entities processing personal data for their own personal interests, so long as they do not disclose or share such personal data with others.
Amidst on-going currents of globalisation and international policy debate about whether privacy is a universal human right and whether global internet governance should address privacy more cogently, this study emerges to furnish an investigation into patterns and implications of privacy perceptions and awareness in Thailand focusing on general users in the online sphere as well as strategic members of civil society.
1. What are the notable characteristics of privacy perceptions and awareness of the Thai public, online and off-line, and how are these perceptions and awareness of privacy as well as reactions to privacy threats among Thai online users influenced by these factors — socio-demographic, cultural attitudes, and Internet use characteristics?
2. Do perceptions and awareness of privacy among users vary in different online applications — SNS, e-commerce websites, online forums, media sharing and blogs? How? Why?
3. What are the perceptions of key members of Thai civil society with regard to online privacy and what advocacy actions, if any, are taken to promote the right to privacy in Thai society?
1. A questionnaire-based survey of 800 samples of Internet users and mobile phone users in six regions of Thailand — North, Northeast, South and Central (main focus in Bangkok and the Metropolitan area) was carried out. Sample groups were screened to include only Internet users, thus purposive sampling applies.
About half of the questionnaires were distributed manually and the other half via the Internet, by posting on locally popular websites such as pantip.com, dekdee.com, kapook.com and mthai.com. The scope of the inquiry in the survey includes:
• socio-demographics of the sampled online users;
• patterns of Internet use of the sampled users;
• socio-cultural attitudes of the sampled users;
• privacy awareness as reported by the sampled users in the general context, and in the online context;
• perceptions of privacy risks and threats in different online application contexts eg email, MMS, SNS, online forums, micro-content networking;
• An assessment of response behaviour in cases of privacy abuses resulting from ICTs uses.
2. In-depth interviews with selected members of civil society who have advocated for rights and liberties and who have worked in the social areas of ICTs, namely, Foundation for Consumers, Telecommunications Consumer Protection Institute, Thai Netizen Network, Campaign for Popular Media Reform, Siam Intelligence Unit and Freedom against Censorship Thailand (FACT).
Of the total number of 800 participants in the survey, 60.9 per cent (487) are male and 37.1 per cent (297) are female. Those in the 16-25 age group represent the largest group of participants at 51.6 per cent (413), followed by those in the 26-35 age group at 28 per cent (324). In terms of income, 34.8 per cent (278) of the samples have a monthly income of USD155-311, while 30.1 per cent (341) earn less than USD155. Only 3.4 per cent (27) earn more than USD1555 USD.
Most of the participants (54 per cent – 432) have bachelor’s degrees while 15.4 per cent (123) have completed secondary education and 12.3 per cent (98) have master’s degrees or higher. With respect to their jobs, 44.8 per cent (358) are students while 27.8 per cent (223) are government officials or employees in state enterprises, followed by 15.3 per cent (122) and 10.9 per cent (87) who are business employees and self-employed, in that order.
As for the pattern of Internet use of the sampled population, the survey finds the following: A greater number of the surveyed users (45 per cent) are heavy users averaging more than three hours of daily use while 24.8 per cent spend an average of 1-2 hours using the Internet. Meanwhile, most of the sampled population appear to be experienced Internet users, with 48.6 per cent having more than six years of Internet use experience, 30.9 per cent having 4-6 years of use of experience, and 15.6 per cent having 1-3 years of experience, respectively. Most of the participants also access the Internet mainly from their home computer (48.9 per cent) while some (29.8 per cent) access the Internet mainly from their office computer and mobile phones (18 per cent). In addition, the survey finds that the most heavily used online applications of the sampled population are as follows (in ranking order): (1) search engines, (2) social networking, (3) electronic mail, (4) online media; and (5) web portals.
In regard to the distribution of cultural attitudes among those surveyed, the study finds most of the respondents to be collectivist[22] (94 per cent), liberalist[23] (82 per cent), localist[24] (77.6 per cent). Meanwhile, 80.3 per cent rank censorship over free expression.[25]
By contrast, only a few respondents appear to be individualist (6 per cent) and conservative (18 per cent). Only 22.4 per cent of respondents subscribe to globalisation over localism.
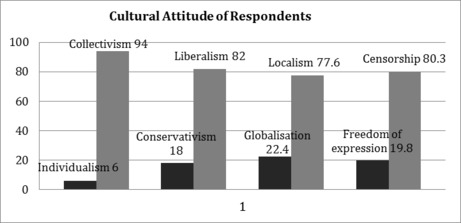 Figure 1:
Distribution of cultural attitudes of survey respondents
Figure 1:
Distribution of cultural attitudes of survey respondents
Based on the survey findings, the sampled population tend to rate their privacy awareness high in these contexts — polling booth privacy, police intrusion, and physical notions of privacy (the right to be let alone). Meanwhile, they rate their awareness about privacy at a medium level in these contexts — surveillance cameras in the workplace, wiretapping for police investigations and quality assurance of services (for example, a conversation recorded by call centre). Lastly, they rate awareness of privacy issues in the following contexts at a low level — consumer database and corporate data sharing, state surveillance such as citizen ID cards and job screening through criminal record checks.
|
Low
|
Medium
|
High
|
|
Consumer database and corporate data sharing
|
Surveillance camera in workplace
|
Polling booth privacy
|
|
State surveillance
|
Wiretapping for police investigation and quality assurance of
services
|
Police intrusion
|
|
Job screening through criminal record checks
|
|
Physical notion of privacy (the right to be let alone).
|
Table 1: Level of privacy awareness in offline contexts
Respondents perceive that these Internet applications, in ranking order, are most prone to privacy violations, social networking applications such as Hi5 and Facebook, email, online media, search engines and electronic commerce websites.

Figure 2: Distribution of levels of perception of online privacy threats across different applications
In a hypothetical context of an online privacy violation, respondents (56 per cent) choose to react to such threat by initiating social movement and public advocacy such as writing letters to media to raise social and public awareness of the threat. Meanwhile, 25 per cent of respondents prefer a technological fix, meaning that they choose to tweak privacy settings available in online applications. Only 19 per cent of respondents would call for more rigorous laws and regulations governing online applications’ policies.
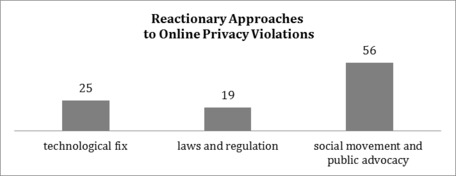
Figure 3: Distribution of different approaches in coping with online privacy violation
If unauthorised use of personal data stored online is known, most respondents (47 per cent) choose to take part in a social movement/campaign to stop it. While nearly an equal proportion of respondents (41.2 per cent) prefer to have policies and laws such as personal data protection laws in response to unauthorised use of data. Only 11.8 per cent of respondents would like to see a tighter self-regulation from online service industry.
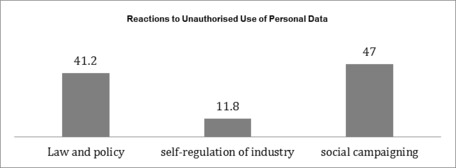 Figure 4:
Distribution of reactionary approaches to unauthorised use of personal data
Figure 4:
Distribution of reactionary approaches to unauthorised use of personal data
Most of the respondents (58.3 per cent) agree that public participation, for example, a call for a data protection law initiated from civic groups or a majority of the population, is needed in order to accomplish personal data protection. Meanwhile, only 16.8 per cent of respondents believe that current personal data protection in the private sector is already sufficient and no personal data protection law is required.
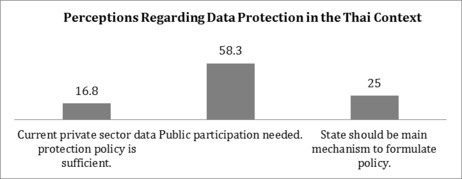
Figure 5: Distribution of different perceptions towards a data protection law in the Thai context
Most respondents (55.4 per cent) value freedom of expression and privacy equally while 23 per cent give greater importance to freedom of expression at the expense of privacy. Only 21.6 per cent of respondents value privacy over freedom of expression.
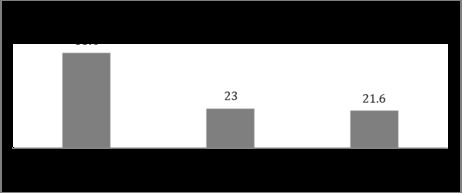
Figure 6: Distribution of balancing between freedom of expression and privacy
In this section, the research team analysed the data by cross-tabulating two sets of collected data and a statistical analysis using both descriptive and inferential statistics to uncover the relationship between postulated variables — socio-demographics, patterns of Internet use, cultural attitudes and perception and awareness of online privacy which also includes reactionary and preventive measures against privacy violations and opinions regarding data protection laws in the Thai context. The analysis shows the following sets of interesting results.
|
|
Collection Limitation
|
Purpose Specification
|
Use Limitation
|
Data Retention
|
|
Social networking websites
|
Strongly agree
(x̄ = 3.77)
|
Strongly agree
(x̄ = 3.89)
|
Strongly agree
(x̄ = 4.02)
|
Strongly agree
(x̄ = 3.82)
|
|
E-commerce websites
|
Strongly agree
(x̄ = 3.54)
|
Strongly agree
(x̄ = 3.82)
|
Strongly agree
(x̄ = 3.89)
|
Strongly agree
(x̄ = 3.81)
|
|
Online forum
|
Strongly agree
(x̄ = 3.76)
|
Strongly agree
(x̄ = 3.86)
|
Strongly agree
(x̄ = 3.90)
|
Strongly agree
(x̄ = 3.74)
|
|
Media sharing
|
Strongly agree (x̄ = 3.76)
|
Strongly agree
(x̄ = 3.82)
|
Strongly agree
(x̄ = 3.90)
|
Strongly agree (x̄ = 3.77)
|
|
Blog
|
Strongly agree (x̄ = 3.50)
|
Strongly agree
(x̄ = 3.68)
|
Strongly agree
(x̄ = 3.75)
|
Strongly agree (x̄ = 3.71)
|
Table 2: Attitude towards privacy principles that should apply across online applications
Findings indicate that respondents strongly agree that every privacy principle, based on OECD’s privacy guidelines, namely, data collection limitation, purpose specification, use limitation and data retention, should be applied in all online applications (ranges from 3.5-4.02).
Privacy awareness in online applications
Based on a set of questions posited to measure the respondents’ privacy awareness in different online applications, the following result is obtained. Overall, privacy concerns are exhibited at the highest level in relation to media sharing websites (x̄ = 3.76), followed by e-commerce websites (x̄ = 3.72), online forums (x̄ = 3.7), and blogs (x̄ = 3.5). But relatively low concern (x̄ = 2.73) about privacy is shown in relation to social networking websites.
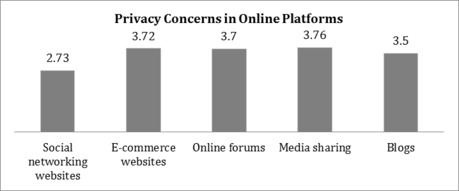
Figure 7: Distribution of levels of privacy awareness across different online applications
The overall mean (x̄) for each application derives from computation of rated answers to a set of questions as explained below.
In terms of privacy settings on social networking sites, respondents have moderate levels of privacy awareness (x̄ = 2.73). They are also highly aware of privacy implications of personally identifying data (x̄ = 3.56). For example, they exhibit caution when they are about to publish sensitive personal data such as private pictures, email, education and workplace details on their walls.
Respondents are highly aware of marketing surveillance (x̄ = 3.72), such as using cookies and stealth applications employed by the websites. They are also highly aware of data matching/profiling of online customers likely to operate within e-commerce sites (x̄ = 3.41). However, in regard to revealing their personal ID online, respondents are moderately cautious about making their personal data visible to the online public.
Respondents are highly aware (x̄ = 3.70) that identifiability of users required by online forums is prone to privacy violations. Similarly, they also agree that the collection of certain personal data such as national identification numbers required by online forums may compromise privacy.
Users of media sharing are highly aware of privacy (x̄ = 3.76) as to a great extent they agree that media sharing websites should not require identifiable personal data from users. In general, respondents disapprove (x̄ = 2.32) of the data collection practices by media sharing websites particularly when it comes to keeping tabs of the videos they view and their use patterns. This shows that they are aware of the privacy risks involved.
Similar to other online platforms, blog users are fully aware of privacy violations (x̄ = 3.50). Respondents do not feel it necessary for blog service providers to require personal data such as name, address and national identification card number. This implies that they do not appreciate the transparency of online personas. Nevertheless, the same percentage of respondents does not think they will subscribe to an anonymous blog space like invisiblog.com, fearing anonymity may compromise responsibility.
By using inferential statistics to analyse the collected data, it is found that there is a statistically significant relationship between the following sets of socio-demographic variables — age and education — and online privacy awareness. Education, in particular, is found to have a positive correlation with privacy awareness in all online applications except online forums (eg sites such as <www.pantip.com>).
Apart from demographic factors, patterns of Internet use are also important factors influencing the level of privacy awareness. Findings indicate that the level of Internet use, frequency of Internet use and length of Internet use experience influence the level of privacy awareness of respondents. Respondents who use the Internet longer, more frequently and have more experience of Internet use are more likely to be aware of online privacy issue than those who use Internet for shorter amounts of time, less frequently and have less experience of Internet use.
According to the findings, there is a statistically significant relationship between all the studied dimensions of cultural attitudes and online privacy awareness. As mentioned earlier, four aspects of cultural attitudes are studied in this research which could be grouped into four dichotomies as follows — collectivism vs individualism, conservatism vs liberalism, localism vs globalisation, and freedom of expression vs national security.
The study finds that those with an individualistic attitude have higher online privacy awareness and are more aware of intrusions to their privacy than those with a collectivistic attitude. Similarly, those with a liberalist attitude show a higher score in online privacy awareness than those with a conservative attitude. In addition, those who are more inclined toward globalisation are also more perceptive and aware of their online privacy and threats to its violation than are those who tend to favour localism. Lastly, those who place more emphasis on freedom of expression than on national security also exhibit higher levels of privacy awareness and threats to privacy than those that think otherwise.
According to our findings, differences in cultural attitudes of the respondents do not affect reactionary approaches to privacy violations. However, the same proportion of those respondents that could be classified as individualistic (56.3 per cent) and collectivist (56.1 per cent) prefer the same reactionary approach — by employing public advocacy and social movement/campaigns — to address privacy violations. In conclusion, respondents pay attention to educating and raising awareness of privacy issues to the public.
The study finds that demographic factors; namely, gender, age, income and education are not associated with reactionary approaches to the privacy violation of respondents. However, the reactionary approach that appeals most to every age group, gender, income group and education level is public advocacy and social movement/campaigns. To conclude, in line with the type of reactionary approach preferred by respondents of different cultural attitudes, the majority of respondents place importance on public education and raising social awareness of privacy issues.
All of the key participants in the interviews conducted by the authors agree that since the rise of the information society and the inception of the Internet, privacy has been almost impossible to sustain. The demarcation between public and private spheres has been blurred with the advent of new social media like Facebook, which has been a potent force in shaping an emerging information-sharing culture. Once the information is shared online, the content owners are unlikely to be able to control the flow of that information.
Most of the interviewees believe that there is no such thing as ‘privacy’ in new media. Even when the best laws apply, no one can guarantee privacy in the online world. Technical defaults in online applications compromise privacy, in many cases without the knowledge of users. Mobile devices such as Blackberry phones are equipped with built-in Global Positioning Systems (GPSs). Once users post anything on Facebook or Twitter, location data will be automatically attached to the end of the post. Yet, very few users seem to care about setting their privacy defaults to prevent such applications from reporting on their location in order to protect their privacy.
Apart from built-in surveillance mechanisms in communication devices, the main privacy issue about which civil society is concerned is the marketing surveillance practices (such as consumer profiling, direct marketing through short messaging services, and spam emails), all of which take advantage of new ICTs. This concern is consistent with research findings from Dhillon and Moore, indicting that respondents’ main issue with online privacy is the potential for websites to sell details of online consumers to a third party.[26]
Most of the key informants interviewed feel that, in the absence of a data protection law, record-keeping organisations, state or private, do not have proper standard procedures for handling personal data. In the case of government agencies, the overarching notion of national security is usually cited to override the right to privacy of data subjects whose records are kept in their files. Moreover, the politically-motivated enforcement of new law like the Computer Crime Act 2007 has spurred a tendency to probe into people’s private data. Provisions of this law, it merits notice, authorises competent officials to inspect computer traffic data and confiscate computer systems of suspects which in turn allow them to access others’ personal information.
Meanwhile, consumer profiling through the matching of data from different corporate databases is said to be a rampant practice in the private sector. While this practice went on unnoticed, one interviewee strongly feels that private corporations stand to lose their reputation if word gets out into the public about such practices. But this same participant also noted that few large corporations with a good public image are unlikely to trade or reveal customer databases to other organisations.
Key business players who have invested much in their corporate image and CSR will likely try to maintain their public perception of themselves by having safeguards for their customers’ private data: Isriya Paireepairit, Siam Intelligence Unit (SIU).
The key members of civil society interviewed are convinced that Thai society generally lacks an awareness of privacy issues due to Thailand’s cultural and historical background. First, they view Thai society as having long been a collective society, where the interest of the collective community is emphasised at the expense of that of the individual’s. Meanwhile, the primarily agrarian and rural culture has not been conducive to inculcating a sense of privacy in a large part of the population. This notion is in line with political scientist Kitiyadisai’s comment that the strength of traditional Thai culture impeded a mass awareness of the of privacy rights.[27]
Even in the more urban parts of the country where people are more individualistic and can afford relatively more private living conditions, these interviewees still feel that privacy is not a choice but rather a luxury for the upper social strata. Oftentimes, privacy is confused with secrecy and the convenience of aspects of an urban lifestyle like credit cards and the like have only helped to make people less aware of the fact that their personal information may be abused.
Secondly, the still underdeveloped notions of civil liberty and the rule of law have also been identified as factors shaping the lack of privacy consciousness. Despite the fact that democratic revolution took place 80 years ago, the Thai public’s understanding of democracy is limited mainly to casting votes at a general election. The realisation of citizenship rights and the exercise thereof still needs to be improved, not to mention the lack of understanding about less inherent rights, such as the right to privacy, in the Thai context.
An average person is not motivated to exercise his or her right and usually would not be able to tell that a privacy violation has occurred: Saree Ongsomwang, Foundation for Consumers.
Third, the lack of awareness and motivation to pursue privacy rights has been exacerbated by the prevalence of privacy violations in the media. The growing trend of tabloidised media has led to substantial sensationalism that dwells on scandals, private lives of celebrities and so forth. In effect, as some of the interviewed activists point out, Thai society has become familiarised and desensitised to privacy-eroding practices.
Furthermore, interviewees commonly feel that the level of privacy awareness depends substantially on how strong the network of consumers is. According to those interviewed, consistent consumer attention and movements will strengthen and enhance privacy awareness in society.
In all, interviewees shared their views on privacy awareness in these dimensions:
This is the area of awareness that is most lacking in Thailand, according to the key interviewees. Since aggregate data collection by the state has been practiced for a long time, Thai people have become familiarised with supplying personal information and having their identification verified as one of their lifelong experiences and activities. Thai citizens are required to apply for national identity cards from the age of seven and must be able to show the cards if requested by government officials, according to the Identity Card Act 1983.[28] However, with technological advances in data collection and manipulation — the change of national ID cards to Smart cards in 2005 — these civic activists seem to express awareness about the risks that may be involved with such a large-scale record-keeping system and the capacity of data manipulation, particularly now that the ID process is extended to children as young a seven years old. But since the ID card is part of a citizenship scheme required by law, there is not much that an average citizen can dispute. The interviewees also expressed concern about privacy in medical records. In its zeal to contain or alleviate public health issues, the Thai health authority often resorts to compiling huge health databases, without first seeking the consent of data subjects.
This is another area of privacy that several participants agree is problematic in Thai society but nevertheless seems to go on unnoticed. Take phone tapping for example; such a practice is unlawful but there is little that the average citizen could do to prove his or her case and to obtain legal redress. According to a communications reform activist who has been working relentlessly for freedom of expression for decades, she has always suspected, and is in fact convinced, that her cell phone is tapped due to her advocacy work. Yet, she could not figure out a way to resolve this. Many activists, she said, suspect the same but are limited in means with which to deal with the problem.
It is almost a common knowledge among NGO workers that their office phone is tapped, and now their cell phones. But we honestly don’t know what to do so we let it be. If we go to the police, they will likely deny. If we go the National Human Rights Commission to file complaint, we must first have our proof of evidence. But how do you get that? In such circumstances, I think helplessness just leads to ignorance or even inertia: Supinya Klangnarong, Campaign for Popular Media Reform.
Apart from zero-in surveillance like phone-tapping, some of these leading activists also voiced concern about large-scale market surveillance, such as spam, SMS, or email.[29] They noted that a large majority of Thai consumers may feel that such practices are a nuisance but they are unaware that these are also violations of right to privacy.
As citizens, they could rightfully demand state agencies to take care of the problem more responsibly. They could also demand stronger rules and regulations. But the problem is they are not aware that they are capable of such action: Dr Pravit Leesathapornvongsa, Telecommunications Consumer Protection Institute.
Given the highly volatile political landscape in Thailand in recent years, the interviewed activists generally feel that abuses of privacy have increased, largely owing to clashes that emanate from divisive politics among the populace, as well as from intensified surveillance by the state.
Cyber-lynching, in which personal information is broadcast for public scrutiny, is viewed as more alarming than surveillance of dissent by the state. The latter is usually carried out as a routine procedure by the state while the former reflects extreme politicisation in which the violation of privacy is a tool for curbing opposing viewpoints and political ideologies.
To me, cyber-witch hunts of dissidents or those with different viewpoints from the mainstream are particularly worrying. It shows that Thai people really have the utmost disrespect for privacy right. To them, privacy is not a fundamental right. Or else they would not resort to such measure in trying to destroy their political enemy: Sarunee Achavananthakul, Thai Netizen Network.
On the one hand, these activists, who generally support freedom of expression, feel that the proliferation of free speech through such means as online forums, social networking websites, and blogs is a positive sign in terms of democratic development. On the other hand, however, they also see that the divisive colour-coated politics[30] in Thailand in the past few years has led to political extremism and that this has contributed negatively to the advancement of rights and liberty for Thai people as the extremists themselves have irresponsibly abused those rights in their democratic struggles.
Insofar as state surveillance is concerned, this has indeed been heightened in the midst of the political crisis and fervent desire for political communication. State surveillance of online political forums has been rampant through the use of so-called cyber cops and automatic surveillance system. In response, many online users who are aware of these surveillance schemes have tried to evade them by using circumvention tools or by resetting their privacy settings. However, one of the key interviewees points out that this is not real privacy awareness, but rather a need to hide their real identities. Instead of protecting citizen’s privacy, the state, through such agencies as the Ministry of Information and Communication Technology (MICT), using tools such as the Computer Crime Act 2007, has been relentless in identifying and prosecuting political dissidents.
The heavy politicisation in the online sphere and the growing amount of cyber witch-hunting has overshadowed violations of privacy in the commercial sphere, which is indeed more widespread. One key interviewee believes that privacy violation in online platforms is more prominent as users, with or without their knowledge, will leave a footprint at some point. Technically skilled computer users will be able to trace the identity and the locale of the user, hence intensifying the surveillance capacity of large organisations — both state and corporate.
While freedom of expression has been at the centre stage of civil rights advocacy for decades, privacy rights have not been given such attention for many reasons. Representatives of civil society interviewed tend to feel that freedom of expression is more easily understood than privacy and has been consistently advocated through the mass media in Thailand to create policy impacts. Furthermore, privacy issues in the modern era are closely intertwined with technology, an area in which few NGOs in Thailand have expertise. Leading NGOs and civic activists in Thailand tend to be associated with areas such as land rights, community rights, environmental rights, food safety, health care, or rights to access drugs — all of which are more tangible than privacy. Even emerging NGOs like the ‘Thai Netizen Network’ which includes the right to privacy in their mission statement, have yet to address privacy directly in their work.[31]
Nevertheless, these leading civil society representatives do feel that it is high time that privacy be advocated more intensively and systematically in Thailand, given all the developments surrounding the information society and the lack of comprehensive laws to guarantee the right to privacy in Thailand. All of the civil society representatives interviewed strongly feel that privacy advocacy should be carried out strategically in the Thai context where privacy is little understood. One interviewee, who has been a staunch advocate for freedom of expression, feels that real-life case studies of privacy violations is a good strategy to advance public understanding of privacy issues.
All social issues that may not be tangible for public understanding (including privacy) start with case studies. To me, this is the most strategic course of action that can be further advanced into social campaign: Supinya Klangnarong, Campaign for Popular Media Reform.
Meanwhile, consumer protection activists believe that in order to maintain awareness of privacy in the minds of the Thai people, it is crucial to link this awareness to something more fundamental such as health, safety, or personal belongings.
According to a well-known and highly respected consumer advocate who leads the Foundation for Consumers, privacy advocates in Thailand should push for the passing of a data protection law as their top priority. If the passage of the law is not immediately feasible, then they should take advantage of other more plausible regulatory avenues such as the rules and regulations or notifications of the newly established communications regulator, the National Broadcasting and Telecommunications Commission (NBTC), which will in turn be enforceable on NBTC licensees. Since the Frequency Allocation and Regulation of Communications Act (2010) has a provision on consumer protection that regulates the privacy practices of broadcast and telecommunications operators, the NBTC thus has a legal obligation to regulate in these areas.
In addition to statutory regulation or regulation by the state,[32] this civic advocate also strongly feels that it is important to push for the self-regulation of industry that is more cognisant of privacy protection.[33] This would involve an industry code of ethics as well as effective enforcement mechanisms that are privacy sensitive. Meanwhile, civil society advocates should work as focal points in creating a multilateral network of partners to raise privacy awareness at the societal level. This network should include civil society, academia, consumer groups, and the media to help monitor cases of privacy violations while attempting to strike a fruitful balance between freedom of expression and privacy in Thai society.
Aside from civil society, another route through which privacy awareness could be improved is through social institutions like family and school. According to a long-standing media reform advocate, such establishments are an integral part of cultivating privacy awareness among younger generations by equipping them with ICT literacy. ‘Family members, school and media are the best institutions to start teaching about privacy’, said the media advocate. According to her, curricula in school ought to be updated to teach children about new developments like ICTs and their consequences. Last, but not least, this activist and her civil society peers commonly feel that political will from government and policy-makers is required to advance the course of privacy protection in Thailand.
The quantitative results of the study show that respondents to the survey have between medium to high levels of awareness of privacy in different online and offline contexts. Interestingly, however, in the context of aggregate surveillance administered by the state, such as through citizen ID cards, and criminal record checks or private organisations such as consumer data mining and sharing, respondents exhibited only medium levels of awareness.
Notably, the measuring of privacy awareness in this study departs markedly from research in the West where privacy is an inherent value and well understood. To assess privacy awareness in the Thai context, where privacy is not a fundamental trait and is little understood, the research team had to build upon concepts from the OECD’s fair information practice principles and operationalise around the different applications or situational contexts to examine the perception and awareness of privacy and related behaviours in Thai society.
When cross-tabulated with a number of postulated factors, the research also finds a statistically significant relationship between age and education and online privacy awareness. Education, in particular, is found to have a positive correlation with privacy awareness in all online applications except online forums. This is consistent with prior studies undertaken by Paine et al (2007)[34] and Leathern (2002).[35] However, gender is found not to affect the level of privacy awareness among respondents, which is in contrast to studies conducted by Hoy and Milne (2010)[36] and Nosko et al (2012).[37] Patterns of Internet use — frequency of use and length of use experience — also have a positive influence on levels of privacy awareness. This is in contrast to a study by Kurt (2010)[38] that found no relationship between frequency and experience of Internet use. However, the relationship between Internet use experience and levels of privacy awareness is consistent with Lohse et al (2000)[39] who discovered that sensitivity to privacy issues online decreased with Internet experience.
Meanwhile, there is a statistically significant relationship between all the studied dimensions of cultural attitudes and online privacy awareness. Respondents who rated high in their privacy awareness are also more predisposed towards these values in their cultural attitudes: individualism, liberalism, globalisation, and freedom of expression. This supports the predominant notion that privacy is premised upon Western values of liberalism, individualism, the public-private divide, and the rule of law.[40]
But the qualitative research shows a rather conflicting picture as leaders of civil society organisations appear more pessimistic, with an impression of little public sensitivity on the issue, due to prolonged history of state surveillance and the conservative nature of Thai society.[41] Some activists voiced concern about the lack of realisation of privacy rights and the feeling of helplessness that may lead to ignorance and inertia. Others are worried about the inadvertent use of cybercrime law and ruthless cyber witch-hunts and the cyber-lynching of political dissidents as major threats to privacy in the online sphere. Here, the activists are focusing more on the instrumental dimension of privacy rather than the substantive dimension,[42] and are localising privacy within the Thai context, which is suffering from an extensive political and ideological divide.
All of the interviewed civic leaders agree on the need for a privacy/data protection law and comprehensive social campaigns to raise awareness about privacy and personal data protection. But they are still vague about strategies to pursue or resources to mobilise, other than that civil society should be a prime force in advocating on the issue. This is in line with Bernier’s recommendation (2012)[43] that civil society should play a role in balancing privacy and national society. Moreover, these civic leaders voice the need to use a human rights discourse within international legal framework to mobilise the protection of privacy[44] and to focus on targets of group pressure and resistance, which is in line with Bennett’s strategies for privacy advocacy.[45]
Although this study has a large number of respondents, the majority of respondents are relatively young (aged between 16 to 35 years old) and most of them are students. This, as a result, suggests that the findings might not accurately reflect the general perception of Thai citizens. However, the population aged 60 and over constitutes only six per cent of total Internet users in Thailand.[46] Accordingly, this segment of the population may be irrelevant to the focus of this research. Future research, however, could expand to cover a wider range of sample age groups.
Questionnaire
1. Email: _____________
Section 1: Demographic
(Question 2-6 Demographic Questions (Please mark ✓ as appropriate)
2. Sex
❍ Female ❍ Male ❍ not specified
3. Age (year)
❍ less than 15 ❍ 16 – 25 ❍26 – 35
❍ 36 – 45 ❍ 46 – 55 ❍ 56 – 65 ❍ over 66
4. Income (per month)
❍ less than 5,000 ❍ 5,000-10,000 ❍ 10,001-20,000
❍ 20,001-30,000 ❍ 30,001-40,000 ❍ 40,001-50,000
❍ more than 50,000
5. Highest Qualification (if studying, select degree pursuing)
❍ less than lower secondary school ❍ lower secondary school ❍ higher secondary school ❍ vocational certificate or equivalent
❍ vocational diploma or equivalent ❍ Bachelor degree
❍ Master degree ❍ PhD
6. Occupation
❍ Student ❍ Government Official ❍ Private company staff
❍ Self-employed ❍ Retired / unemployed ❍ Others (please specify) __
Section 2: Internet Usage Pattern
Please mark ✓ as appropriate
(Question 7-10 Internet Usage Patterns)
7. Your daily Internet surfing
❍ less than 1 hour ❍ 1 – 2 hours ❍ 2 – 3 hours
❍ more than 3 hours
8. Your weekly Internet surfing
❍ everyday ❍ nearly everyday (5 - 6 days/week)
❍ 3 - 4 days/week ❍ 1 - 2 days/week ❍ hardly use/no use
9. How long have you been using the Internet? (please estimate)
❍ less than 1 year ❍ 1 – 3 years ❍ 4 – 6 years
❍ more than 6 years
10. How do you connect to Internet? (select as many as appropriate)
❍ PC or Notebook from home ❍ PC or Notebook from work
❍ Mobile phone
❍ Others such as IPad or electronic devices capable of connecting to Internet such as PSP, Nintendo DS
11. Please indicate 5 applications that you use through the Internet (1 means most use/2 means less use than 1).
|
|
Online newspaper, radio, television (eg, bangkokpost.com,
channel3.co.th)
|
|
|
Search engine (eg, google.com, ask.com)
|
|
|
Portal web (eg, yahoo.com, sanook.com)
|
|
|
Online shop (eg, tarad.com, thaionlinemarket.com)
|
|
|
Internal organization information exchange website
|
|
|
Social network sites (eg, Hi5, Facebook)
|
|
|
Online forum (eg, pantip.com, thaiskywebboard.co.th)
|
|
|
Email (eg, gmail, yahoomail or organisation/university email)
|
|
|
Blog (eg, bloggang, exteen, oknationblog or special interest blog)
|
|
|
Microblog (eg Twitter)
|
|
|
Media sharing (eg, youtube.com, flicker.com)
|
|
|
Wiki (eg, wikipedia or wikileaks)
|
Section 3: Measuring Social Attitude
Please mark ✓ as appropriate
(Question 12-20 Measuring Social Attitudes: Society and Culture)
12. People in the country will be living in harmony and peace if the minority preserve their different attitude and behaviour from the majority for public interest (individualism vs. collectivism).
❍ agree ❍ don’t agree ❍ not sure
13. If relatives need financial help and it is unlikely that they will be able to repay, we should help as much as we can (individualism vs. collectivism).
❍ agree ❍ don’t agree ❍ not sure
14. Sex before marriage or cohabitation is normal today (liberalism vs. conservatism).
❍ agree ❍ don’t agree ❍ not sure
15. Seniority systems or patron-client systems is an obstacle to the development of Thai society (liberalism vs. conservatism).
❍ agree ❍ don’t agree ❍ not sure
16. Thai values have deteriorated because of Thai people’s exposure to foreign media (globalisation and localism).
❍ agree ❍ don’t agree ❍ not sure
17. Government should have the right to stop publishing, broadcasting of media outlets with strong political affiliations due to national security concerns (freedom of expression vs. national security).
❍ agree ❍ don’t agree ❍ not sure
18. Using Blackberries, drinking Starbucks and eating Korean food are new practices of Thai teenagers that adults must learn to accept (globalization vs. localism).
❍ agree ❍ don’t agree ❍ not sure
19. Website blocking and filtering by the government is not appropriate as it violates the right of people to communicate (freedom of expression online).
❍ agree ❍ don’t agree ❍ not sure
20. As there are many religions in Thailand, every important religious date should be a public holiday (liberalism vs. conservatism).
❍ agree ❍ don’t agree ❍ not sure
21. Movies with nudity, violence and insulting remarks to the monarchy should be banned (freedom of expression vs. conservatism).
❍ agree ❍ don’t agree ❍ not sure
22. The Prime Minister’s reconciliation plan is a solution for Thai society (individualism vs. collectivism).
❍ agree ❍ don’t agree ❍ not sure
23. Communication through computers and the Internet creates new words such as ‘chimi, kri kri’ and may ruin the Thai language (globalization vs. localism).
❍ agree ❍ don’t agree ❍ not sure
Section 4: Attitude to Privacy
Please mark ✓ as appropriate
(Question 24 – 30 measuring awareness of privacy as a right in general)
|
Passage
|
Strongly Agree
(5)
|
Agree (4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree
(1)
|
|---|---|---|---|---|---|
|
24. It is normal practice, for private companies to share clients’
personal information, eg name, address and telephone with
others as it is now
the information society era and this is not considered a violation of consumer
rights. (market surveillance)
Negative
|
|
|
|
|
|
|
25. ID cards are a form of surveillance in Thai society as the state will
be able to check personal identity. (state’s bureaucratic
surveillance)
|
|
|
|
|
|
|
26. It is acceptable if the state and corporations check applicants’
criminal records without their consent as it is a part
of a filtering system to
find good employees. (data surveillance/criminal record database)
|
|
|
|
|
|
|
27. Media coverage of actors, actresses or celebrities’ stories is
permissible as they are public figures. (privacy of public
persona)
Negative
|
|
|
|
|
|
|---|---|---|---|---|---|
|
28. Installation of CCTV in the workplace is a violation of
employee’s privacy (workplace surveillance)
|
|
|
|
|
|
|
29. It is essential that voting be anonymous so that nobody knows a
voter’s choice. (secrecy of the ballot box)
|
|
|
|
|
|
|
30. Police must obtain a warrant before entering people’s dwellings,
it will be considered a violation of privacy otherwise.
police
surveillance)
|
|
|
|
|
|
|
31. Not only is it illegal for any person or organisation to make use of
your personal information without consent but it also violates
human dignity.
(privacy on human dignity)
|
|
|
|
|
|
|
32. You always lock your door when staying in private rooms, eg bedroom and
office (privacy as right to be let alone)
|
|
|
|
|
|
|
33. Phone tapping for the purpose of state investigation or for monitoring
employee’s work, eg call centre, is a normal practice.
Negative
|
|
|
|
|
|
Section 5: Measuring awareness in Internet privacy
34. From a list of Internet applications, please rate from highest to lowest the risk that your personal information and privacy will be violated. (1 is the highest risk 2 is lower risk and 5 is the least risk)
|
|
Online newspaper, radio, television (eg bangkokpost.com,
channel3.co.th)
|
|
|
Search engine (eg, google.com, ask.com)
|
|
|
Portal web (eg, yahoo.com, sanook.com)
|
|
|
Online shop (eg, tarad.com, thaionlinemarket.com)
|
|
|
Internal organisation information exchange website
|
|
|
Social network sites (eg, Hi5, Facebook)
|
|
|
Online forum (eg, pantip.com, thaiskywebboard.co.th)
|
|
|
Email (eg, gmail, yahoomail or organization/university email)
|
|
|
Blog (eg, bloggang, exteen, oknationblog or special interest blog)
|
|
|
Microblog (eg, Twitter)
|
|
|
Media sharing (eg, youtube.com, flicker.com)
|
|
|
Wiki (eg, wikipedia or wikileaks)
|
35. Measuring perception and awareness in privacy right on Internet applications (Please mark ✓as appropriate)
How do you agree with the statements below?
Online Shopping
|
Statements
|
Strongly Agree
(5)
|
Agree
(4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree (1)
|
|
1) Collection limitation
Client databases compiled from online orders should contain only email
addresses, not physical addresses.
|
|
|
|
|
|
|
2) Purpose specification
Online shops need to provide a reason for requesting personal information
from clients.
|
|
|
|
|
|
|
3) Use limitation
Having provided personal information, clients should be able to decide
whether that information may be used or shared —particularly
with third
parties for marketing purposes.
|
|
|
|
|
|
|
4) Data retention
A section in the Computer Crime Act stating that Internet service
providers must keep Internet traffic data for at least 90 days in order to
identify users is necessary
particularly for e-commerce websites. Negative
|
|
|
|
|
|
|
5) Using cookies on e-commerce websites that keep clients’ personal
data without their knowledge is a form of violation of consumer
information
privacy. (online market surveillance/cookies)
|
|
|
|
|
|
|
6) Apart from requesting clients to give their personal information, some
websites also automatically keep clients’ ‘footprints’
on the
web and match them with personal information to develop a client profile
database for segmentation advertising. Such practices
may bring benefits to the
target group and should not be considered a violation of information privacy.
(consumer surveillance/ data
profiling) Negative
|
|
|
|
|
|
|
7) You prefer to use websites equipped with secure payment and encryption
systems that have international credibility eg paypal and
Ebay.
|
|
|
|
|
|
|
8) Some online shops in Thailand require a client’s email, address
and personal information to be published publicly, but this
is standard practice
on Thai websites and should not be a problem. (openness of system)
Negative
|
|
|
|
|
|
Online Forums
|
Statements
|
Strongly Agree
(5)
|
Agree
(4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree (1)
|
|
1) Collection limitation
Personal data maintained by online forum operators should contain only
email addresses, not physical addresses.
|
|
|
|
|
|
|
2) Purpose specification
Online forum owners need to provide a reason when they request personal
information from clients.
|
|
|
|
|
|
|
3) Use limitation
Having provided personal information, users should be able to decide
whether that information may be used or shared —particularly
with third
parties for marketing purposes.
|
|
|
|
|
|
|
4) Data retention
A section in the Computer Crime Act stating that Internet service
providers must keep Internet traffic data for at least 90 days in order to
identify users is necessary
particularly for online forums. Negative
|
|
|
|
|
|
|
5) Some online forums have developed logins to be something more than to
simply grant a user access to post messages. For example,
the login for
pantip.com has been linked to email and Facebook, which will enable public to
identify the actual user. Negative
|
|
|
|
|
|
|
6) Some political online forums require users’ to register using
their ID cards before they can post messages. This practice
violates privacy.
(ID-verification system)
|
|
|
|
|
|
|
7) Using pseudonyms in online forums prevents users from being identified
and allows them full freedom of expression without fear.
However, this will lead
to a denial of responsibility when posting messages on online forums.
Negative
|
|
|
|
|
|
|
8) There should be a law requiring online forums to set up a clear personal
information privacy policy, eg identifying how personal
data will be stored,
providing a password protection measure and allowing users to check the accuracy
of their personal information
(data-protection/privacy policy
requirement).
|
|
|
|
|
|
Blogs
|
Statements
|
Strongly Agree
(5)
|
Agree
(4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree (1)
|
|
1) Collection limitation
Databases maintained by blog services should contain only email addresses,
not physical addresses.
|
|
|
|
|
|
|
2) Purpose specification
Blog service providers must inform bloggers of the reasons why their
personal information is required.
|
|
|
|
|
|
|
3) Use limitation
Having provided personal information, bloggers should be able to decide
whether that information may be used or shared —particularly
with third
parties for marketing purposes.
|
|
|
|
|
|
|
4) Data retention
A section in the Computer Crime Act stating that Internet service
providers must keep Internet traffic data for at least 90 days in order to
identify users is necessary
particularly for blogs. Negative
|
|
|
|
|
|
|
5) A condition for registration for blogs, like Oknation, a citizen
journalism blog, that require that personal information such as
name, address
and ID number be submitted is crucial to this type of blog. Negative
|
|
|
|
|
|
|
6) Anonymous blog services, like invisiblog.com, which do not require a
user’s real identity or picture, are available. You
think that this type
of blog is interesting and would like to subscribe to it.
|
|
|
|
|
|
|
7) You think that blog service providers should offer privacy functions
which allow bloggers to control whether other bloggers view
their blogs.
Negative
|
|
|
|
|
|
|
8) Blog service providers should provide tools to allow blog owners to
limit access to non-members or non-authorised users and to
hide blogs from
search engines.
|
|
|
|
|
|
Online Social Networks
|
Statements
|
Strongly Agree
(5)
|
Agree
(4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree (1)
|
|
1) Collection limitation
Personal data in user profiles should consist of only email addresses
rather than data that can be used to identify people.
|
|
|
|
|
|
|
2) Purpose specification
Online social network sites must inform users of the reasons why their
personal information is required.
|
|
|
|
|
|
|
3) Use limitation
Having provided personal information, users should be able to decide
whether that information may be used or shared — particularly
with third
parties for marketing purposes.
|
|
|
|
|
|
|
4) Data retention
A section in the Computer Crime Act stating that Internet service
providers must keep Internet traffic data for at least 90 days in order to
identify users is necessary
particularly for social networking websites.
Negative
|
|
|
|
|
|
|
5) While using social networking sites, you set privacy levels to
‘public’, the minimum privacy level, in order to facilitate
meeting
new people online. Negative
|
|
|
|
|
|
|
6) You always upload personal data linked to yourself — eg photos,
emails, education and employment information to your profile.
Negative
|
|
|
|
|
|
|
7) You are more cautious when posting photos that may be interpreted
negatively eg drinking photos, smoking photos.
|
|
|
|
|
|
|
8) You only accept friend requests on Facebook if you know that person.
|
|
|
|
|
|
Microblogs
|
Statements
|
Strongly Agree
(5)
|
Agree
(4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree (1)
|
|
1) Collection limitation
Personal data on microblogs like Twitter should consist of only email
addresses rather than data that can be used to identify people.
|
|
|
|
|
|
|
2) Purpose specification
Microblog sites must inform users of the reasons why their personal
information is required.
|
|
|
|
|
|
|
3) Use limitation
Having provided personal information, microblog users should be able to
decide whether that information may be used or shared —
particularly with
third parties for marketing purposes.
|
|
|
|
|
|
|
4) Data retention
A section in the Computer Crime Act stating that Internet service
providers must keep Internet traffic data for at least 90 days in order to
identify users is necessary
particularly for microblog websites. Negative
|
|
|
|
|
|
|
5) When using microblogs such as Twitter, you set your privacy to allow
only your followers to view your broadcast messages.
|
|
|
|
|
|
|
6) Retweeting your messages or personal opinions by others to unknown
people is a violation of your privacy.
|
|
|
|
|
|
|
7) You always tweet content that represents yourself, eg data, photos,
video clips of current activities. Negative
|
|
|
|
|
|
|
8) On your profile page, you reveal your identity, eg occupation,
political views, and favourites in order to attract people. Negative
|
|
|
|
|
|
Media Sharing
|
Statements
|
Strongly Agree
(5)
|
Agree
(4)
|
Neutral
(3)
|
Disagree
(2)
|
Strongly Disagree (1)
|
|
1) Collection limitation
Personal data in user accounts in media sharing sites, eg youtube or
flickr, should consist of only email addresses rather than data
that can be used
to identify people.
|
|
|
|
|
|
|
2) Purpose specification
Media sharing sites must inform users of the reasons why their personal
information is required.
|
|
|
|
|
|
|
3) Use limitation
Having provided personal information, users of media sharing sites should
be able to decide whether that information may be used
or shared —
particularly with third parties for marketing purposes.
|
|
|
|
|
|
|
4) Data retention
A section in the Computer Crime Act stating that Internet service
providers must keep Internet traffic data for at least 90 days in order to
identify users is necessary
particularly for media sharing sites. Negative
|
|
|
|
|
|
|
5) Storing how video clips are viewed by youtube users is beneficial and
harmless as youtube can utilise this data to recommend video
clips to users in
the future. Negative
|
|
|
|
|
|
|
6) Uploading a clip of your friend on the beach wearing a bikini and adding
‘young lady on the beach’ as a description
does not require
permission from your friend.
|
|
|
|
|
|
|
7) Uploading secretly filmed video clips of government officials, eg
constitutional court cases, is a good thing as it lets people
know what
happened, although the person who has been filmed might not be aware of being
filmed. Negative
|
|
|
|
|
|
|
9) Downloading pictures from media sharing sites such as flickr.com
conveniently helps journalists and individuals to find certain
people’s
pictures even the people downloading such pictures do not actually know those
people. Negative
|
|
|
|
|
|
Section 6: Measuring prevention and reaction behaviour when privacy is violated.
Please mark ✓as appropriate
1. When a friend posts what you consider to be inappropriate material on Facebook (eg personal messages, information or by tagging you in photos to show other people), what would you do? (reaction)
a. Adjust your privacy settings or block that friend because he/she violated your privacy. (1)
b. Post a warning or message on your status so that Facebook users will not engage in such behaviour. (2)
c. Send a message to Facebook asking for a clear and effective measure to prevent privacy violations. (3)
d. Other (please specify) ...........................................
2. Would you use identical passwords for all email accounts? (prevention)
a. Yes and it will be an easy password because of convenience. (1)
b. Yes but will be a difficult password — otherwise someone may easily hack my account. (2)
c. No, as it is not safe. (3)
3. When using Twitter, would you indicate the location from where you are tweeting? (prevention)
a. No, as I do not want anyone to know where I have been. (3)
b. Yes, so my followers know where I am tweeting from. (1)
c. I will both tell and not tell my location, depending on the locations (2)
4. If network administrator in your organisation checks and deletes data in your mailbox, you would... (reaction)
a. File a complaint indicating that this act is a violation of privacy. (3)
b. Do nothing as I do not want to have an argument with my organisation. (1)
c. Forward anonymous emails to the Internet community and other people I know in my organisation, explaining the act as a privacy violation. (2)
d. Other (please specify) ...........................................
5. Would you link data from one website to another, eg using Google when logging in to gmail? (prevention)
a. No, because those websites will then know about my personal life. (3)
b. Yes, because it is more convenient. (1)
c. Only on a case-by-case basis as I am not sure about how this affects privacy. (2)
6. What should be done to solve the problem of using personal data from e-commerce websites without permission? (reaction)
a. There should be some sort of punishment in law. (3)
b. Websites should invent a clear measure to protect personal data. (1)
c. E-commerce websites should inform everyone to be vigilant when giving out personal data. (2)
d. Other (please specify) ...........................................
7. What would be your Twitter conditions for followers? (prevention)
a. Obtaining my permission first, as I only want to share my story with particular people.
b. Allowing everyone to follow my Twitter so they can view my broadcast messages.
c. Allowing everyone to follow my Twitter, but I will delete followers once I consider that they should not be able to see my tweets.
8. What is your opinion about Internet privacy protection laws in Thailand (law and principle)
a. Government should be responsible for drafting and enforcing all related law. (3)
b. People must participate in drafting, passing and enforcing Internet privacy protection laws.
c. There is no need for a law as websites can manage privacy protection on their own.
9. If you found out the content published in your personal blog is searchable through an Internet search engine by key words, you would... (reaction)
a. Love it, and keep checking if search engines can still find my blog.
b. Be angry and prevent search engines from finding my data by using robots.txt file which will make search engines overlook my domain name.
c. Do nothing.
10. Julian Assange, founder of Wikileaks, refers to freedom of information and the right to information when he published confidential documents and secrets on Wikileaks. What do you think? (law and principle)
a. Agree and support the release of information on Wikileaks
b. It depends on the case and whether it serves the public interest or is a privacy violation.
c. Do not agree as it creates a public sphere for legitimate privacy violations.
1. How do you assess the current privacy situation in Thailand?
2. How do you assess the level of privacy awareness in Thai society? In terms of information privacy and communication?
3. How do you assess the violation of privacy in Thai society?
4. What is the best way to advocate for privacy in Thailand?
5. Does your organisation manage to advocate fro privacy in any way? How?
[*] Assistant Professor, Faculty of Communication Arts, Chulalongkorn University Email: <pirongrong.r@chula.ac.th> and pirongrong.r@gmail.com>.
[**] Lecturer, School of Communication Arts, University of the Thai Chamber of Commerce and PhD candidate at the Faculty of Communication Arts, Chulalongkorn University. Email: <sopark_pan@utcc.ac.th> and
<soparks@live.com>.
(This work was supported by the Higher Education Research Promotion and National Research University Project of Thailand, Office of the Higher Education Commission (HS1231A). The authors of this article would also like to express gratitude to the International Development Research Council (IDRC) of Canada through the PrivAsia Project for funding this research.)
[1] Doug Tygar, ‘Technological dimensions of privacy in Asia’ (2003) 10 Asia-Pacific Review 121, 120-145.
[2] Up until the 1940s, Thailand was known as Siam. The name change occurred during the dictatorial rule of Field Marshal Plaek Phibunsongkram who advocated the new country’s name on grounds of modernisation.
[3] Thailand has had at least 15, failed as well as successful, coups d’état since the country shifted from absolute monarchy to constitutional monarchy in 1932. The latest coup took place on 19 September 2006 when civilian and highly popular Prime Minister, Thaksin Shinawatra, was toppled by a military junta, the Council for Democratic Reform (later changed to the Council for National Security).
[4] This Directive (95/46/EC) states that the EU will not trade with countries without adequate protection of personal data on the third countries. As a result, many countries were prompted to adopt a new policy and regulatory approach towards personal data, mostly in digital forms.
[5] The National Identity Card Act 1983 requires Thai citizens between 15 and 70 years of age to apply for national identity card at local council. All national identity card holders’ personal data is then recorded into an online computer system which can be accessed by government officials. As a new microchip embedded card has been introduced recently, more personal data can be recorded directly to the card without the cardholders’ knowledge. With regard to public surveillance cameras, in Bangkok alone, nearly 30 000 CCTV units have been installed. Without data protection laws in place, abuses of large pools of personal data are beyond citizens’ control.
[6] Pirongrong Ramasoota, ‘Information Technology and Bureaucratic Surveillance: A Case Study of the Population Information Network (PIN) in Thailand’ (1998) 51 Information Technology for Development 51, 54.
[7] Nithima Kananidhinand, Awareness of information privacy rights in Internet communication in Thailand (Master thesis, Department of Journalism, Faculty of Communication Arts, Chulalongkorn University, 2001) 131.
[8] Dara Hallinan, Michael Friedewald and Paul McCarthy, “‘Citizens’ Perception of Data Protection and Privacy in Europe’ (2012) 28 Computer Law & Security Review 263, 265.
[9] Landsdowne Market Research, Public awareness survey 2008, Data Protection Commissioner, Portarlington, Ireland, (2008)
<http://www.dataprotection.ie/documents/press/survey08.pdf> , cited in ibid.
[10] Hallinan, Friedwald and McCarthy, above n 8, 265.
[11] According to the UK Office of Communications’ (Ofcom) research report on social networking, social networking sites offer people new and varied ways to communicate via the Internet, whether through their PC or their mobile phone. They allow people to easily and simply create their own online page or profile and to construct and display an online network of contacts, often called ‘friends’. Users of these sites can communicate via their profile both with their ‘friends’ and with people outside their list of contacts. This can be on a one-to-one basis (much like an email), or in a more public way such as a comment posted for all to see. See more in Ofcom, Social Networking: A Quantitative and Qualitative Research Report into Attitudes, Behaviors, and Use, 2 April 2008.
[12] Data obtained from <http://www.socialbakers.com/blog/647-top-10-biggest-facebook-cities> .
[13] Mehmet Kurt, ‘Determination of Internet Privacy Behaviours of Students’ (2010) 9 Procedia Social and Behavioral Sciences 1245, 1246-48.
[14] Carina Paine et al, ‘Internet Users’ Perception of ‘Privacy Awareness’ and ‘Privacy Actions’ (2007) 65 International Journal of Human-Computer Studies 526, 530-32.
[15] Nosko et al, ‘Examining Priming and Gender as a Means to Reduce Risk in a Social Networking Context: Can Stories Change Disclosure and Privacy Setting Use When Personal Profiles Are Constructed?’ (2012) 28 Computers in Human Behavior 2067, 2071.
[16] Mariea Grubbs Hoy and George Milne, ‘Gender Differences in Privacy-Related Measures for Young Adult Facebook’ (2010) 10 Journal of Interactive Advertising 28, 40.
[17] The two suspects were arrested and charged with spreading online rumors about the King’s health during the panic selling in the local stock market earlier this month. The Computer Crime Act s 14 allowed action against computer users spreading information deemed detrimental to national security or false information that could cause panic among the public.
[18] Palrak Raksaphol, Police arrest two suspects in stock rumour case (1 November 2009) <http://ireport.cnn.com/docs/DOC-348877> .
[19] Information privacy as used in this study refers to the ability of an individual to control when, how, and to what extent information about him or her is communicated to others as well as the control of access to his or her personal information. Meanwhile, communication privacy refers to the ability of an individual to control the interception or disclosure of his or her communication without authorisation.
[20] Bangkok Pundit, ‘Abhisit’s SMS Message’, Asian Correspondent (online), 19 December 2008 <http://asiancorrespondent.com/19743/abhisits-sms-message/> .
[21] The PDRC is an umbrella political pressure group in Thailand that was formed in November 2013. Its aim is to remove the influence of former premier Thaksin Shinawatra from Thai politics and to create an unelected ‘People’s Council’ to oversee political reforms. The group played a leading role in the 2013–14 Thai political crisis, organising large-scale protests within Bangkok and a few Southern provinces.
[22] Collectivism here is explored in contrast with individualism as opposing dichotomies for cultural attitudes. While an individualist person is characterized by an I-consciousness, a predisposition towards task over relationship, and a right to privacy, a collectivist person would be characterized more by a WE-consciousness, a preference of relationship over task, and a stress on belonging. See more in Harry C Triandis, Individualism & Collectivism: New Directions in Social Psychology (Westview Press, 1995) 259.
[23] Liberalism is positioned here as opposed to conservatism, with exclusive focus on social views. A liberal person tends to favour change or things that gravitate from a normative tradition or the status quo while the opposite would be true for a conservative person. For instance, a liberal person would support equal rights to gays, legal abortion, and restriction or regulation of the right to bear arms. But a conservative person would hold the opposite views on these issues. See more in <http://www.diffen.com/difference/Conservative_vs_Liberal> .
[24] Localism is explored here in contrast with globalisation. Localism usually describes social measures or trends which emphasise or value local and small-scale phenomena. This is in contrast to large, all-encompassing frameworks for action or belief. Localism can therefore be contrasted with globalisation, and in some cases localist activism has parallels with opposition to corporate-led globalisation. See <http://en.wikipedia.org/wiki/Localism_%28politics%29> .
[25] Thailand has historically been a ‘security state’. The country’s modern political history was shaped as a buffer state between the Free World and the Soviet Bloc due to its strategic geographical location in Indochina. See more detail in Pasuk Phongphaichit and Chris Baker, Thailand: Economy and Politics (Oxford University Press, 1995).
[26] Gurpreets Dhillon and Trevor Moores, ‘Internet Privacy: Interpreting Key Issues’ (2001) 14(4) Information Resources Management Journal 33, 35.
[27] Krisana Kitiyadisai, ‘Privacy Rights and Protection: Foreign Values in in Modern Thai Context ’ (2005) 7 Ethics and Information Technology 17, 17.
[28] Privacy International, Report: Thailand Chapter IV Privacy Issue
<https://www.privacyinternational.org/reports/thailand/iv-privacy-issues>.
[29] Sending electronic spam is actually a crime according to s 11 of the Computer Crime Act 2007, which reads ‘Any person sending computer data or electronic mail to another person and covering up the source of such aforementioned data in a manner that disturbs the other person’s normal operation of their computer system shall be subject to a fine of not more than one hundred thousand baht’. However, to date, there are no reports of any cases that have been based on this provision.
[30] The continued political crisis in Thailand in the past few years has been dubbed by international observers as ‘color-coated politics’ between the yellow-shirts and the red-shirts which represent opposing political ideologies and interests. The ‘Yellow Shirts’ or the People’s Alliance for Democracy (PAD) is the royalist movement that has rallied against the former Prime Minister — Thaksin Shinawatra, who was ousted in a military coup in 2006. The ‘Red Shirts’ or the United Front for Democracy against Dictatorship (UDD) which support the ousted Thaksin are against the military and have been accused of disloyalty to the royal establishment. Meanwhile, to some local observers, these two opposing forces have also become a reflection of the clash between an urban middle class on one side and the rural poor on the other.
[31] Even in the Thai Netizen Network’s recently published manual of Internet users, safety is emphasised as the top issue while privacy is included under that rubric: see Thai Netizen Network, Manual for Internet Use for Netizens (Khu meu Phonlamuang Net) (Heinrich Boell Foundation, 2013).
[32] According to Millwood-Hargrave, self-regulation and co-regulation are viable models of regulation for digital media which are widely diffused, robust, and relying more on audience-interaction. See more in M Millwood-Hargrave, More Trust in Content — the Potential of Co- and Self- Regulation in Digital Media, (Report for Working Group 3 of the Conference of Experts for European Media Policy, Leipzig, May 9-11, 2007) 24.
[33] Also, the NBTC is mandated by law (the 2008 Broadcasting Act) to promote media professionals into self-regulatory organisations that will in turn promulgate a code of ethics and put into effect a system of self-regulation.
[34] Paine et al, above n 15, 533.
[35] Rob Leathern, FTC Security Workshop Security and Privacy Data (20 May 2002) <http://www.ftc.gov/bcp/workshops/security/020520leathern.pdf> .
[36] Hoy and Milne, above n 17, 28.
[37] Nosko et al, above n 16, 2067.
[38] Kurt, above n 14, 1246-48.
[39] Gerald Lohse, Steven Bellman and Eric Johnson, ‘Consumer Buying Behavior on the Internet: Findings from Panel Data’ (2000) 14 Journal of Interactive Marketing 313, 320.
[40] Colin J Bennett, Regulating Privacy: Data Protection in the United States and Europe, (Cornell University Press, 1992) 15.
[41] Chris Baker and Pasuk Phongpaicjit, A History of Thailand (Cambridge University Press, 2009).
[42] Charles Fried, ‘Privacy’ (1968) 77 Yale Law Journal 475, 480.
[43] Chantal Bernier, ‘The integral role of civil society in balancing privacy and national security’ Remarks at the 2012 International Intelligence Review Agencies Conference (30 May 2012) <http://www.priv.gc.ca/media/sp-d/2012/sp-d_20120530_cb_e.asp> .
[44] Quirine Eijkman, ‘Mobilizing for Privacy: Civil Society Advocacy against Surveillance in the Netherlands’ (2012) 5 Journal of Politics and Law 42, 46.
[45] Colin J Bennett, The Privacy Advocate: Resisting the Spread of Surveillance, (MIT Press, 2008).
[46] National Statistical Office, ICT in Thai Households
<http://service.nso.go.th/nso/nsopublish/themes/files/ict_hh55_pocket.pdf> .
AustLII:
Copyright Policy
|
Disclaimers
|
Privacy Policy
|
Feedback
URL: http://www.austlii.edu.au/au/journals/JlLawInfoSci/2014/5.html